STRATEGIC SECURITY EVALUATION
Take Awareness to the Next Level
In one Forrester survey, only 40% of organizations indicated their current risk management strategies are effective.*
Fully documenting your security posture is an important step when trying to effectively govern risk. Our Strategic Security Evaluation offers a comprehensive overview—facilitated by expert technical resources—of your security stack across endpoints, networks, data, cloud, and compliance. This service provides clear guidance on your security capabilities and a roadmap to help you close defensive risk. Get the coverage your enterprise deserves. Start with a Strategic Security Evaluation today!
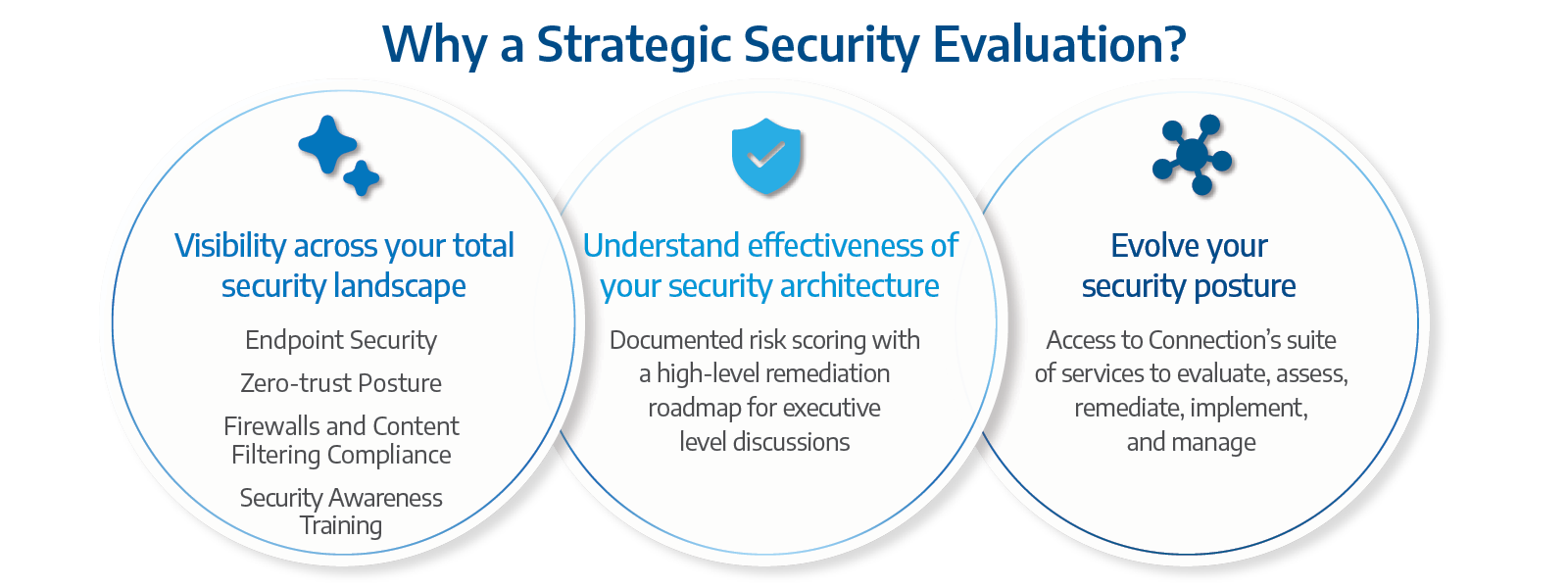
Our Approach to the Strategic Security Evaluation
Our cybersecurity consultants conduct interviews to identify and document risks without using technical tools or agents. This includes assessing your current security technology, processes, policies, and tools. Post-interview, you’ll receive a report with a prioritized risk summary and a segmented risk roadmap for success.Connection will collect an inventory of implemented security controls—including security technology, documentation, and processes. We will also evaluate the implementation of the security controls to determine the defensive capabilities of your systems.

Change Happens. EXPERTISE WINS.™
Get expert guidance from Cybersecurity Specialists that have decades of experience understanding the security needs of organizations.Strategic Security Evaluation Deliverables
- Documented risk scoring in a single view that provides a risk ranking for each security domain, as well as an aggregated score for the entire ecosystem
- Actionable reporting with a prioritized risk summary organized by criticality, detailing the highest risks across endpoint, network, compliance, data, cloud, and operational security domains
- Vendor agnostic recommendations tailored to your organizational needs, perfect for C-level discussions detailing how to achieve organizational security objectives
Add-ons
- Cyber defense heatmap of defensive capabilities, functions, and control maturity by NIST CSF 2.0, cross referenced to the Zero Trust pillars
- Visual representation of your data source and alerting coverage to associated tactics, techniques, and procedures within the MITRE ATT&CK framework
- Threat profile that contains the details of the common tactics, techniques, and procedures utilized by threat actors likely to target your business vertical

Why Connection?
Connection offers products, technical expertise, services, and solutions to help your business adapt to the ever-changing technology landscape. We drive innovation through delivery and deployment, and by leveraging our knowledge, we can help to ensure you optimize your investments and improve ROI by reducing risks and costs.
Ready to talk about Cybersecurity Compliance Solutions?
Call a Connection expert today.
Let’s Connect!
Share your email and a Connection Cybersecurity Expert will reach out to you during our business hours.Connection Community
TechSperience Episode 144: Future...
In this episode, the Connection Security Center of Excellence team looks beyond today’s headlines to uncover the threats most people... Read More
How St. John’s Health and Connection Are...
In the heart of Jackson Hole, Wyoming, St. John’s Health stands as a beacon of care for both its local... Read More
Securing the Future: Key Insights on...
We recently hosted a webinar with Jamal Khan, Chief Growth and Innovation Officer at Connection and Head of the CNXN... Read More
TechSperience Episode 140: Signals of...
In this episode, the Connection Security Center of Excellence Team takes us on a journey—both literal and technical—sharing insights gained... Read More
Data Security and Compliance: Strengthening...
Data security is a critical priority for everyone, especially those who manage sensitive information across a variety of workstreams within... Read More




